Securing the Software Distribution System
Introduction
AIT’s Fleet Data Command Center SaaS solution (FDCC-SaaS) is a highly secure, reliable, and continuously available cloud-hosted application that works together with AIT’s Portable Data Loaders (PDLs) to provide operators the ability to efficiently manage the configuration and distribution of Field Loadable Software (FLS) from a central library out to aircraft systems throughout the fleet. Additionally, FDCC-SaaS, working together with AIT PDLs can also be used to download and collect logs and data from aircraft systems for storage in a secure central repository.
This blog post addresses how AIT’s FDCC-SaaS and PDLs ensure end to end security for the FLS that is distributed through the system to loadable aircraft LRUs.
FLS Distribution Process
The avionics systems of commercial airliners have become increasingly software based. These systems often require regular software updates in the field (i.e,Nav. Database and Terrain Database updates). Large airline operators are typically operating 100’s of aircrafts, with each aircraft requiring the proper configuration of dozens of software parts. As a result, operators commonly have 100s of PDLs in use throughout the world by their aircraft maintenance teams. To efficiently distribute software parts across widely dispersed fleet PDLs, a network-based distribution system such as a FDCC-SaaS solution is often used.
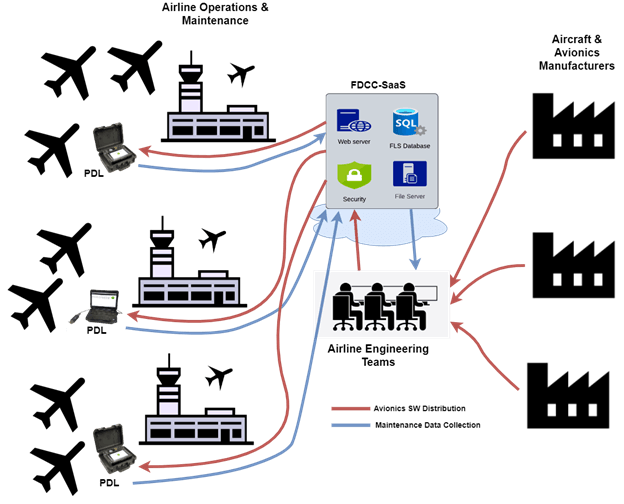
As described in the preceding paragraph and depicted in the diagram above, the system for distributing FLS’ to aircraft systems is complex with many moving parts. A new FLS is released by the manufacturer 8-9 days before it needs to be installed and active on the aircrafts, and therein begins the scramble to get it securely and efficiently loaded onto the aircraft. The FLS is downloaded from the manufacturer, electronically and over a network, and stored onto the software distribution system application (FDCC-SaaS). After the FLS is validated by flight operations, the administrator electronically distributes (over multiple networks) to network-connected PDLs dispersed across several aircraft terminals. The airline maintenance operator then loads the scheduled FLS’ to all of the various aircrafts and onboard systems. As described, the FLS is moved across multiple networks and through several electronic systems (computers, PDLs, etc) on its journey to the aircraft system.
Inside an operation with 100’s of aircrafts across many locations, the process is complicated as each FLS touches a multitude of people and systems. In addition to the complexity of this expansive software distribution process, the attack surface available to persons with malicious intent increases exponentially. There are many more systems and networks available for attack due to the increased need to load more software, more often. Ultimately, this increases the risk exposure for airline operators.
How AIT is Securing the Software Distribution System
To counteract the many threats that can be introduced into aircraft maintenance operations and to safeguard our customers from malicious intent, AIT has integrated industry best practices into our hardware and software solutions as it pertains to cybersecurity. The rest of this post will focus on the comprehensive security features and functions we have built into our portable data loaders (PDLs) and our Fleet Data Command Center SaaS (FDCC-SaaS) solution.
Minimizing or Eliminating Physical Media
The latest Cybersec recommendations and regulations strongly discourage the use of portable media as it introduces security risks into operations. One considerable benefit of using a software distribution platform like AIT’s FDCC-SaaS is to provide the capability of minimizing or completely eliminating the need for physical media that can be lost or compromised. It provides a fully controlled data path throughout operations and allows organizations to seamlessly support Cybersec recommendation and regulation requirements.
Ultimately, this modern approach provides a comprehensive end to end process to manage the acquisition, distribution, loading and monitoring of FLS’ and databases across a global fleet and eliminate, or significantly minimize, the use of insecure and archaic physical media from the data loading process.
SaaS Provides Best-in-Industry Cybersecurity Best Practices
A primary benefit of SaaS is that it is considered by industry experts to be more secure and reliable than most on-premises solutions. SaaS service providers invest heavily in security and have state-of-the-art cybersecurity resources with in-house IT expertise to manage them. They also provide robust disaster recovery solutions with multiple data centers that store business data in geographically dispersed data centers. Continuity of service is assured, SaaS SLAs come with a guaranteed uptime agreement that are customized to your requirements.
In addition to best-in-industry cybersecurity practices, your FLS’ and data will also benefit from best-in-class business continuity with built-in high availability, providing a 99.999 uptime SLA.
In the next few sections, we will dive into the cybersecurity best practices as implemented by our SaaS partner (Microsoft Azure) pertaining to User Authentication & Access Management, Encryption, and use of a Dedicated Application Host.
User Authentication & Access Management
User authentication is a security process that verifies the identity of a user, device, or system trying to access a service or resource. It ensures that the user’s identity is valid and authorized to perform specific actions. AIT’s FDCC-SaaS Solution leverages Azure Active Directory (Azure AD) to provide our customers with protection to authenticate users and control access to our software solution.
Azure AD is a cloud-based identity and access management service from Microsoft and provides several key benefits and functionalities for our clients:
Single Sign-On (SSO) – enables users to access many services and applications using a single set of credentials. This eliminates the need for users to remember and manage separate usernames and passwords for each application, improving convenience and productivity.
Identity and Access Management (IAM) – allows you to centrally manage user identities and access privileges. You can create and manage user accounts, assign roles and permissions, and enforce strong authentication methods such as multi-factor authentication (MFA). This helps enhance security and control over access to your company resources.
Application Management – supports the integration and management of various applications, including AIT’s FDCC-SaaS. Administrators can easily provision and deprovision user access to our application, ensuring streamlined user onboarding and offboarding processes.
Conditional Access – offers robust conditional access policies that allow you to enforce granular access controls based on conditions such as user location, device health, and risk level. This enables you to define and enforce adaptive security measures, such as requiring multi-factor authentication for certain user roles or restricting access from specific IP ranges, thus reducing the risk of unauthorized access.
Reporting and Auditing – provides comprehensive reporting and auditing capabilities to track user activities, sign-in events, and access attempts. This information helps identify security risks, detect suspicious activities, and ensure compliance with regulatory requirements.
By incorporating Azure AD into our FDCC-SaaS application, it simplifies identity and access management, enhances security, and improves productivity by providing a centralized platform for managing your user identities, access controls, and authentication across our application and services used by your company.
Data is Safely Encrypted
Transparent data encryption (TDE) is leveraged by our Azure-hosted FDCC-SaaS application to encrypt the Azure SQL Database. This encryption is known as “encrypting data at rest”. This protects your organization from a malicious party who may steal physical media like drives or backup tapes and try to restore or attach the database and browse its data.
This solution encrypts your sensitive data and uses a certificate to protect the keys that encrypt the data. This solution prevents anyone without the keys from using the data. TDE protects data at rest, which is the data and log files.
Additionally, AIT PDLs data storage system leverage data-at-rest encryption to protect all FLS’ on the PDL as well as data retrieved from the aircraft. If an attacker were to open our PDL and remove the storage to examine it with intent to maliciously tamper, the storage media would be unintelligible. The encryption keys are stored securely on the Trusted Platform Module embedded in the motherboard of our PDL’s.
Dedicated Application Host
As a feature of our FDCC-SaaS application, we provide our customers with a dedicated Azure Application Service instance and an Azure SQL Database instance. This feature provides our customers with a fully isolated and dedicated environment for running FDCC-SaaS securely at a high scale. Customer files (FLS, LSP, and attachments) and data are isolated with secured network access.
You achieve isolation at both the compute-level and the network-level, ensuring that your instances and databases don’t share virtual machines with other customers. It keeps workloads fully contained within a secure native virtual network.
PDL’s Leverage Trusted Platform Module Technology
Trusted platform module (TPM) technology helps keep PCs secure by offering hardware-level protection against malware and sophisticated cyberattacks. TPM’s use cryptography to help securely store essential and critical information on PCs to enable platform authentication.
TPM is embedded security technology (microcontroller) that resides within AIT’s PDL motherboards to securely store artifacts used to authenticate the platform. They store a variety of sensitive information, including user credentials, passwords, certificates, encryption keys, or other important consumer documentation behind a hardware barrier to keep it safe from external attacks. They ensure platform integrity by taking and storing security measurements of the boot process.
From the moment the AIT PDL is powered on, it is guaranteed that only authorized software is allowed to run on the device. This root of trust starts with the TPM and the bootloader. The bootloader is responsible for finding and starting the main Operating System (OS) for the device and for verifying that the OS is being started from a trusted source. This is achieved by the bootloader in verifying digital signatures are in place within the OS files before they are loaded and executed. The next section will cover digital signatures in depth.
Finally, our PDLs are built with enhanced electronic access controls which provide disconnection from ground networks (wired & wireless) during all aircraft load operations. They also incorporate detailed logging of all operations and access attempts for additional auditing and security precautions.
Application of Digital Signatures in the Data Load Process
Digital Signatures provides a method of protecting a piece of software or data against undetected manipulation. ARINC 835 provides guidelines and mechanisms for ensuring the integrity of Loadable Software Parts (LSP’s). With digital signatures applied into practice properly, any new aircraft software should be signed as soon as possible after it was created. The objective is to protect the software against both accidental corruption and malicious tampering as soon as possible after creation. Airline software providers should validate the integrity of the software part before it is made available to its customers or partners.
Digital Certificates are used to ensure the identity of the Aircraft Software Provider (ASP), and therefore, the authenticity of the software. It is recommended that PDL’s check the digital signatures of LSP’s as soon as they are stored on the PDL and right before they are to be loaded onto the aircraft. This ensures that only valid and unaltered LSP’s are made available for maintenance operators to load onto an aircraft.
Please review a recent webinar (Application of Digital Signatures in the Data Load Process) to learn further details about the digital signature process.
Summary
The data load operation and security landscape that operators have been accustomed to is rapidly changing. The PDL and a corresponding software distribution system are necessary tools that are the last line of defense before malicious intent can be carried out against aircraft systems. It is vitally important that airline personnel are trained in security and the use of technologies like PKI and Digital Signatures and are mindful of security best practices throughout each step of their operation. Airline operators must have tools that support and utilize these technologies so that they can drive compliance with these developing guidelines and requirements to ensure business continuity and secure operations moving forward.
AIT’s incorporation of cybersecurity best practices in the design and manufacture of our PDL family and corresponding FDCC-SaaS software and data distribution solution demonstrates our commitment to help our customers securely safeguard their operations while efficiently and cost effectively meeting their data load requirements. AIT has a wealth of experience integrating our solutions within corporate IT systems as well as a proven approach working with IT personnel to ensure our solutions satisfy their cybersecurity requirements.
Interested in more information about AIT’s FDCC-SaaS:
For FDCC-SaaS pricing and availability, please contact .








